Novel Security-Aware Routing (SAR) Algorithm

Building a Comprehensive Network Vulnerability Analysis System: From Topology Design to Real-Time Monitoring
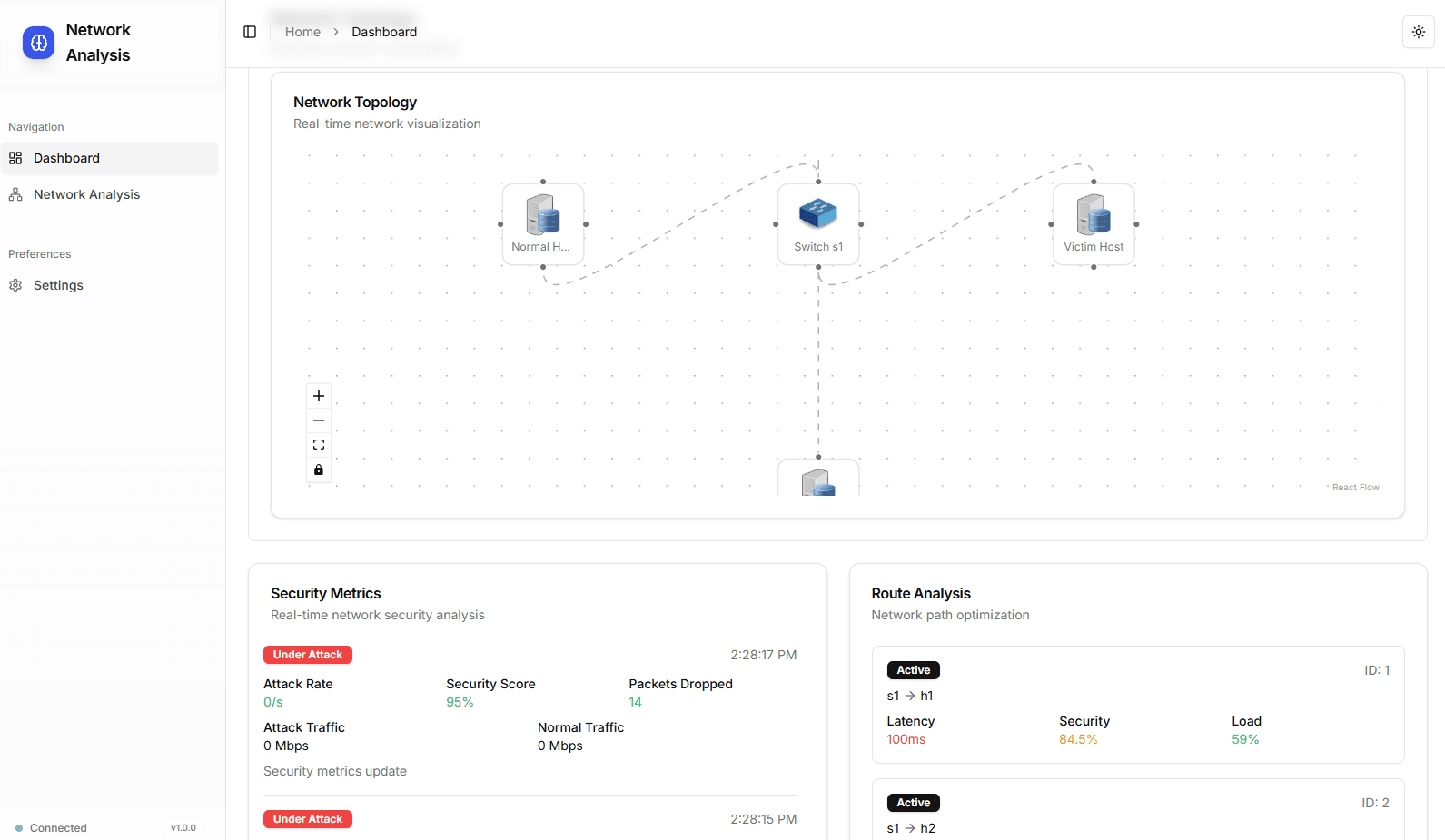
In today's interconnected world, understanding network vulnerabilities before they become security incidents is crucial. That's why we've developed a sophisticated Network Vulnerability Analysis System that allows cybersecurity professionals and network administrators to create, simulate, and monitor network topologies in real-time.
What Makes This System Special?
Our Network Vulnerability Analysis System isn't just another network monitoring tool—it's a complete ecosystem that bridges the gap between theoretical network design and practical vulnerability assessment. The system enables users to:
- Design custom network topologies using an intuitive drag-and-drop interface
- Run realistic network simulations using industry-standard tools like Mininet
- Monitor live events as they happen during simulation runs
- Analyze vulnerability patterns through comprehensive event logging
The Power Behind the Interface
Interactive Topology Editor
At the heart of our system lies a powerful topology editor built with React Flow. This isn't your typical network diagramming tool—it's a sophisticated interface that allows you to create complex network architectures with just a few clicks. Whether you're designing a simple office network or a complex enterprise infrastructure, the editor provides the flexibility and precision you need.
Real-Time Event Monitoring
Once your topology is ready, the magic begins. Our system doesn't just create static diagrams; it brings your networks to life through simulation. Every packet transmission, connection attempt, and potential vulnerability is captured and displayed in real-time, giving you unprecedented visibility into your network's behavior.
Comprehensive Run History
Every simulation run is meticulously tracked and stored. You can review past analyses, compare different topology configurations, and identify patterns that might indicate systemic vulnerabilities across your network designs.
Technical Architecture: Built for Scale and Reliability
Our system follows a modern, microservices-based architecture that ensures both performance and maintainability:
Frontend Excellence
The user interface is built on Next.js, providing a responsive and intuitive experience. The topology editor leverages React Flow for smooth, interactive network design, while real-time updates are powered by Supabase subscriptions that instantly reflect simulation events and run status changes.
Robust Backend Services
Our FastAPI-powered backend serves as the central nervous system, orchestrating communication between the frontend interface and simulation engines. It handles topology submissions, manages simulation lifecycle, and processes event streams with enterprise-grade reliability.
Advanced Simulation Engine
The simulation layer utilizes Mininet, the industry-standard network emulation platform, running in isolated virtual environments. This setup provides realistic network behavior simulation while maintaining complete safety and isolation from production systems.
Cloud-Native Data Management
All simulation data, events, and run histories are stored in Supabase, a modern PostgreSQL-based platform that provides both robust data persistence and real-time capabilities. This ensures that your analysis data is always available and automatically synchronized across all system components.
Getting Started: From Setup to First Analysis
Prerequisites You'll Need
Setting up the system requires a few key components:
- A modern development environment with Node.js and Python
- VirtualBox for running isolated network simulations
- A Supabase account for data management
- The official Mininet VM image for realistic network emulation
The Setup Process
The installation process is streamlined into clear phases:
Database Initialization: Set up your Supabase project and create the necessary database schema for storing simulation runs and events.
Frontend Configuration: Install dependencies and configure environment variables to connect with your backend services and database.
Backend Deployment: Set up the FastAPI service with proper database connections and simulation endpoint configurations.
Simulation Environment: Configure the Mininet VM with proper networking settings and install the simulation components.
Network Configuration Considerations
One crucial aspect of the setup involves properly configuring network bridges between your host system and the Mininet VM. This ensures that simulation events can flow back to your analysis dashboard while maintaining security isolation.
Real-World Applications
Security Assessment
Use the system to model your actual network infrastructure and identify potential attack vectors before they become real threats. The simulation environment allows you to safely test various scenarios without impacting production systems.
Training and Education
Create controlled environments for cybersecurity training, allowing students and professionals to experiment with network configurations and observe the security implications of different design choices.
Compliance Verification
Demonstrate network security measures to auditors and compliance officers by showing how your network architecture responds to various threat scenarios.
Research and Development
Develop and test new security tools and techniques in a controlled environment that can accurately simulate real-world network conditions.
The Workflow in Action
Here's how a typical analysis session unfolds:
Design Phase: Open the topology editor and create your network architecture using the intuitive drag-and-drop interface.
Submission: Once satisfied with your design, submit the topology to the backend for processing.
Simulation Initialization: The system creates a new simulation run record and initializes the Mininet environment with your specific topology.
Live Monitoring: Watch as your network comes to life, with real-time events streaming to your dashboard showing traffic patterns, connection attempts, and potential security events.
Analysis: Review the complete event log, identify patterns, and export results for further analysis or reporting.
Looking Forward
This Network Vulnerability Analysis System represents a significant step forward in proactive network security. By combining intuitive design tools with powerful simulation capabilities and real-time monitoring, it provides security professionals with the insights they need to build more secure, resilient networks.
Whether you're a security researcher exploring new attack vectors, a network administrator validating design decisions, or an educator teaching the next generation of cybersecurity professionals, this system provides the comprehensive analysis capabilities you need.
The future of network security lies not in reactive measures, but in proactive analysis and understanding. With tools like this Network Vulnerability Analysis System, we can move from simply responding to threats to anticipating and preventing them.
Ready to start analyzing your network vulnerabilities? The complete source code and detailed setup instructions are available on GitHub, making it easy to deploy your own instance and begin exploring the security characteristics of your network infrastructure.